Academic research contributes greatly to developments surrounding online privacy and cybersecurity, at times influencing the design of everyday technologies. Our ongoing commitment to security and privacy drives us to continuously learn—and to consider any discoveries with curiosity and transparency.
A paper titled Bypassing Tunnels: Leaking VPN Client Traffic by Abusing Routing Tables was presented earlier this month at the USENIX Security Symposium. It revealed a security vulnerability in VPNs known as TunnelCrack.
There were two attacks described in the paper: The ServerIP attack and the LocalNet attack. Both attacks can be exploited when a user connects to an untrusted Wi-Fi network by tricking the victim into sending traffic outside the protected VPN tunnel. Here’s a summary of these two attacks.
Following a thorough evaluation, we can confirm that these vulnerabilities have had minimal impact on our services. We have also implemented improvements to our systems based on areas of agreement with the researchers, prior to the publication of these findings.
We extend our appreciation to the study authors for reaching out to our security team for the responsible disclosure of their findings prior to the paper’s release. Their collaboration allowed us to promptly investigate potential risks and take measures to strengthen our systems.
What we improved
We are pleased to report that our apps performed as designed, effectively blocking traffic when necessary. The authors found that ExpressVPN was not vulnerable to the ServerIP attack at all, highlighting the strength of our security measures. All of our apps also blocked user traffic when subject to the LocalNet attack, except iOS. (In fact, all of the 67 VPNs tested were found to be vulnerable to this attack on iOS.)
Prior to the publication of the paper, we verified the researchers’ findings and confirmed that it impacts the ExpressVPN iOS app only. We deployed a fix on July 17, 2023 (iOS version 11.105.0), and encourage users to update to the latest version of their iOS app.
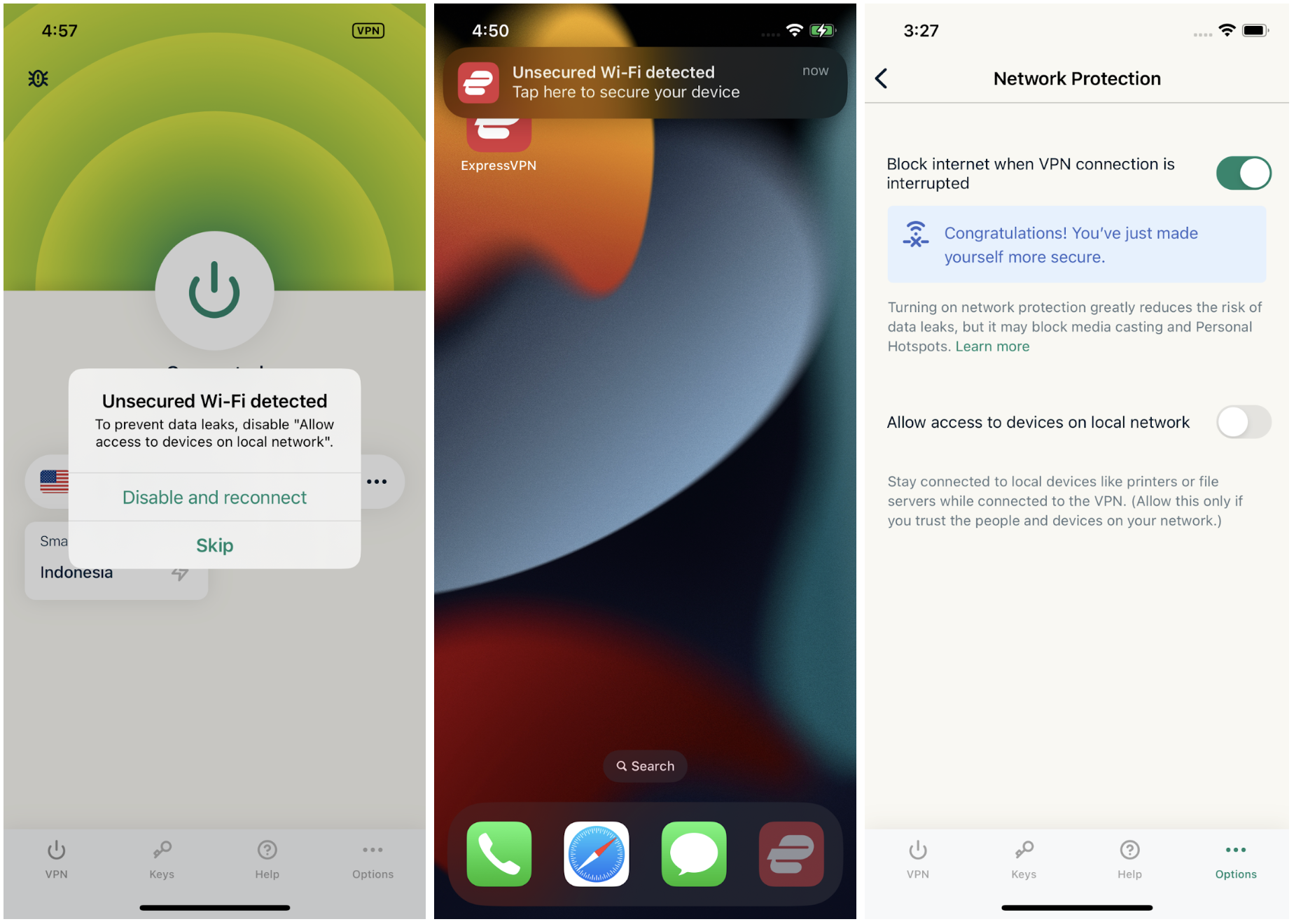
This update introduces a user notification feature specifically designed to detect instances where they may be connected to a Wi-Fi or local network vulnerable to LocalNet attacks. The notification reminds users to review and adjust their settings for optimal protection, allowing users to make decisions based on their preferences.
Users who wish to protect themselves against a potential LocalNet attack can do so by enabling the “Block internet when VPN connection is interrupted” toggle and disabling the ”Allow access to devices on local network” toggle (refer to the third screenshot above).
We’d like to reiterate that the LocalNet attack does not affect our VPN apps on other platforms, and the ServerIP attack does not affect any of our platforms.
Apple’s API challenges and need for improved functionality
The paper also highlights the limitations of Apple’s APIs in addressing traffic leaks in iOS. We agree with this assessment and join the call for Apple to address these issues, which has been echoed by others in the industry. There is a recognized need for improvements in Apple’s APIs, specifically in striking the right balance between functionality and security.
The promise and challenges of Apple’s VPN APIs
To illustrate the challenges, let’s examine the case of iOS 14. With this update, Apple introduced the “includeAllNetworks” option in its APIs to enhance security by directing all data through the VPN tunnel. However, this approach caused unintended disruptions to other iOS functionalities: local printing, AirDrop, CarPlay, AirPlay, and more.
Apple then introduced the “excludeLocalNetworks” option to preserve local functionalities while directing traffic over the VPN. However, Apple’s APIs struggle to reliably direct all traffic securely while consistently offering the expected functional conveniences.
Apple has suggested the “Always On VPN” feature as a potential solution, but it is primarily designed for company-managed devices and not accessible to individual users or commercial VPN providers, making it impractical for the majority of VPN users.
Improving Apple’s APIs on iOS traffic leaks will not only benefit VPN users but also contribute to a safer and more reliable online experience for all Apple device users. Researchers and industry experts have long advocated for improvements in these critical APIs, which will enable developers to create enhanced applications and services within a better ecosystem.
Additional context on the research
With over 14 years of experience in helping users protect their online privacy and security, we at ExpressVPN have gained valuable insights and would like to share more context and nuances to the researchers’ findings.
Recognizing the benefit of allowing local traffic
In the scenario described by the authors, there are concerns about the drawbacks of blocking all local traffic, such as accessing essential services on local networks and receiving security alerts.
However, in real-world scenarios, many crucial services on mobile devices rely on internet-based push notifications, which are not affected by local traffic restrictions. Additionally, in typical environments, the IP addresses assigned are usually compliant with the RFC1918 standard, ensuring accessibility to local resources.
While concerns about blocking all local traffic are valid, they represent edge cases rather than the norm.
By allowing local traffic, we strike a balance between security and accessibility, offering enhanced protection without compromising users’ ability to access essential services.
Strengthening protection measures through blocking non-RFC1918 traffic
As a security measure, we only allow access to local networks that use standard IP ranges known as RFC1918. These ranges, such as 192.168.x.x, 10.x.x.x, and 172.16.x.x to 172.31.x.x, are universally recognized and are commonly used by legitimate networks in trusted environments, such as at home or at work.
By restricting access to recognized IP ranges, we actively defend against potential attacks, including TunnelCrack. Networks outside of these ranges, as demonstrated in the researchers’ attack scenarios, are more likely to be unconventional or potentially malicious.
An exploration of security from all angles
We appreciate the authors’ contribution to the cybersecurity community. It serves as a valuable reminder of the ever-evolving nature of technology, and the importance of collaboration and continuous learning.
Engaging in discussions around the findings can contribute to cybersecurity development more broadly, allowing for a more comprehensive understanding of the vulnerability identified.
Our commitment to maintaining the highest security standards remains unwavering, and we value feedback from stakeholders as we strive to create a safer digital environment for everyone.

30-day money-back guarantee


























Does the “IOS” problem manifest itself on the Graphene OS?
A “permanent kill switch” (or “Always On VPN”) option in your Windows VPN client would be a great addition. It would effectively block any connections going outside the VPN at boot time and/or if the VPN client crashes. This is very doable using the Windows Filtering Platform (WFP).