ExpressVPN blog
Your destination for privacy news, how-to guides, and the latest on our VPN tech

Latest Posts
-

ExpressVPN adds Network Insights and Secure Device Assistant
Your privacy is personal, and the tools that protect it should feel that way too. Our latest updates focus on the small details that shape everyday use, giving you a greater overview of your protected...
-

Zeus virus (Zbot malware): What it is and how to stay protected
The Zeus virus is best known for fueling large-scale financial cybercrime and stealing banking credentials. Although the original Zeus virus is no longer active, it spawned numerous variants that rema...
-
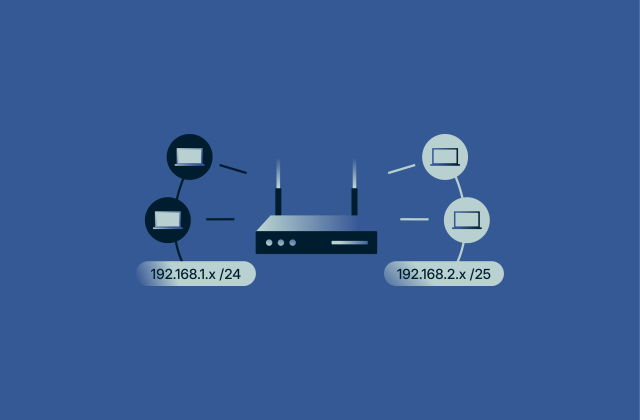
What is a subnet mask? Why it matters for your network
Every device on a network needs a way to know where information should go. Without clear rules, data would move blindly, causing confusion and slowdowns. Subnet masks are one of the tools that make ne...
Featured
See allFeatured Video
-

Top 10 video games that will change how you view privacy
If you love online gaming and are interested in privacy, check out these video games that involve hacking, cybersecurity, and surveillance. Not only are they fun, but they’re designed to give...







